File interceptors
Exchanging files over the internet comes with numerous risks. This applies both to files sent to someone in your organization and files someone in your organization sends out. To mitigate these risks, you may want to vet files uploaded to a conversation before they’re made available to other participants.
The types of risk vary depending on whether your organization is sending or receiving a file:
-
Security risks: A visitor may upload a file containing a virus. If the visitor isn’t authenticated, you know nothing about the person uploading the file.
-
Data leakage: An agent may attempt to upload a file containing internal information or another customer’s personal identifying information (PII). This may happen inadvertently, by selecting the wrong file to upload.
-
Legal requirements: In addition to safeguarding the data of your organization and its customers, there may be legal requirements in place that determine which types of content may or may not be shared in a conversation.
-
Content moderation: Malicious participants may try to upload inappropriate content to a conversation.
File interceptors help you to mitigate each of these risks.
File interceptors work on all files uploaded to conversations, for example:
-
Files uploaded by participants and bots
-
Files uploaded with an external messenger such as WhatsApp
-
Files downloaded during co-browsing sessions
-
Snapshots taken during calls
File interceptors are called after Unblu checks the uploaded file against com.unblu.filemanager.fileTypeWhitelist and com.unblu.filemanager.fileTypeBlacklist.
How file interceptors work
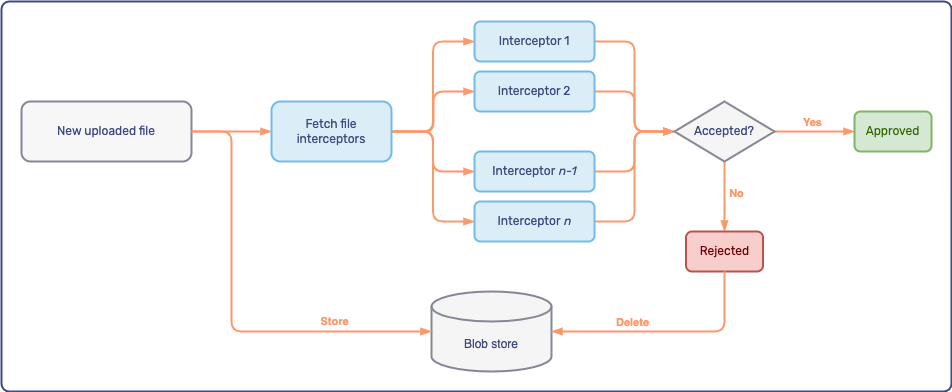
The diagram below shows how the file interception process works:
-
When a participant uploads a file to a conversation, Unblu first stores the file in the Unblu account’s blob store.
-
Next, Unblu retrieves the file interceptors configured for the account and then sends each file interceptor a
file_upload_interceptor.new_filewebhook.The file interceptors are called sequentially, in the order you assigned each of them.
The webhook doesn’t contain the file itself. Rather, it contains some basic information about the uploaded file—such as its name, MIME type, and size—as well as a unique token and a download link. The system that checks the file can use the token and the download link to retrieve the file.
The download link points to the Unblu server, which then retrieves the file from the blob store. File interceptors don’t need access to the blob store. While the file interceptors are reviewing the file, the conversation UI displays a message that the file is being scanned.
-
Once a file interceptor finishes reviewing the file, it calls one of the following web API endpoints:
The call must include the token that Unblu sent the file interceptor in the webhook event. Once Unblu receives a request on one of the endpoints above, the token is invalidated and can no longer be used to download the file with the download link.
-
If all file interceptors approve the file, it becomes available to the participants in the conversation.
If a file interceptor rejects the file, Unblu deletes the file from the blob store and displays a message to all participants that the file was rejected.
If you configure a quarantine blob store for intercepted files that haven’t been approved yet, the process differs slightly.
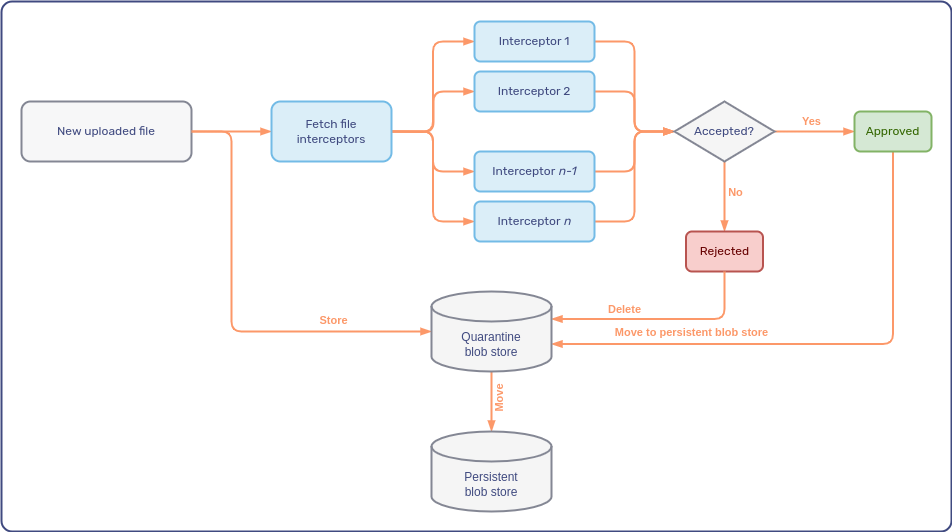
In this case, once all file interceptors have given their approval, Unblu transfers the uploaded file from the quarantine blob store to the persistent blob store.
Configuring file interceptors
Configuring file interceptors mostly consists of creating and enabling or disabling them.
There are two configuration properties for file interceptors:
-
com.unblu.fileuploadinterceptor.scanning.requestTimeout specifies the minimum time that the Collaboration Server should wait for a file interceptor to approve or reject a file before it rejects the file.
-
com.unblu.fileuploadinterceptor.scanning.timeoutJobInterval in the
GLOBALscope defines the cleanup interval for the file scanning request log.
Additionally, you can configure Unblu to store intercepted files in a separate blob store until they’ve been approved. This is described in Configuring a quarantine blob store for intercepted files.
Creating and managing file interceptors
You can create and manage file interceptors in the Account Configuration interface and through the FileUploadInterceptors endpoints of the Unblu web API. Refer to the documentation linked above for more information.
Disabling file interceptors
You can disable file interceptors in the Account Configuration interface:
-
Click the file interceptor in the file interceptor overview.
-
Click the Enabled switch to disable the interceptor.
-
Click Save to save your changes.
Alternatively, you can use the /fileuploadinterceptors/update web API endpoint.
Disabling (and enabling) a file interceptor takes effect immediately. If you disable a file interceptor, files uploaded to ongoing conversations will no longer be processed by the interceptor in question.
Global file interceptors
You can define file interceptors that are used by all accounts on an Unblu installation. Such global file interceptors are defined in the Global Configuration interface (GCi). The GCi also gives you access to the logs of any global file interceptors you’ve enabled.
If you enable a global file interceptor, it’s applied to every file intercepted by any account on the Unblu server, regardless of the file interceptors defined on the individual accounts. If the global file interceptor isn’t configured correctly, every file upload to every account is rejected.
See also
-
For information on creating and managing file interceptors in the Account Configuration interface, refer to the Account Configuration interface guide.
-
For information on the web API endpoints available for file interceptors, refer to the web API reference.
-
For information on the basic checks Unblu runs before calling file interceptors, refer to Configuring file uploads.
-
For information on configuring a quarantine blob store for files that haven’t been approved yet, refer to Configuring a quarantine blob store for intercepted files.