Integrating Unblu with the Airlock Web Application Firewall without protected resources
The Airlock Gateway is one of the security products expressly supported by Unblu for securing public internet access to Unblu installations. This article describes how to configure an Airlock Gateway to upload resources such as CSS files, images, and fonts securely to the Collaboration Server via the SecureFlow Manager (SFM).
| There are three guides for configuring the Airlock Gateway. Go through the checklist to choose the appropriate instructions for your use case before you start configuring the Airlock Gateway. |
Before you start
Before you start, verify that your current installation meets the requirements to run Unblu with Airlock Gateway.
-
For the Unblu server, make a note of following configuration properties:
You need them when you configure the mapping for the Unblu server in the reverse proxy settings.
-
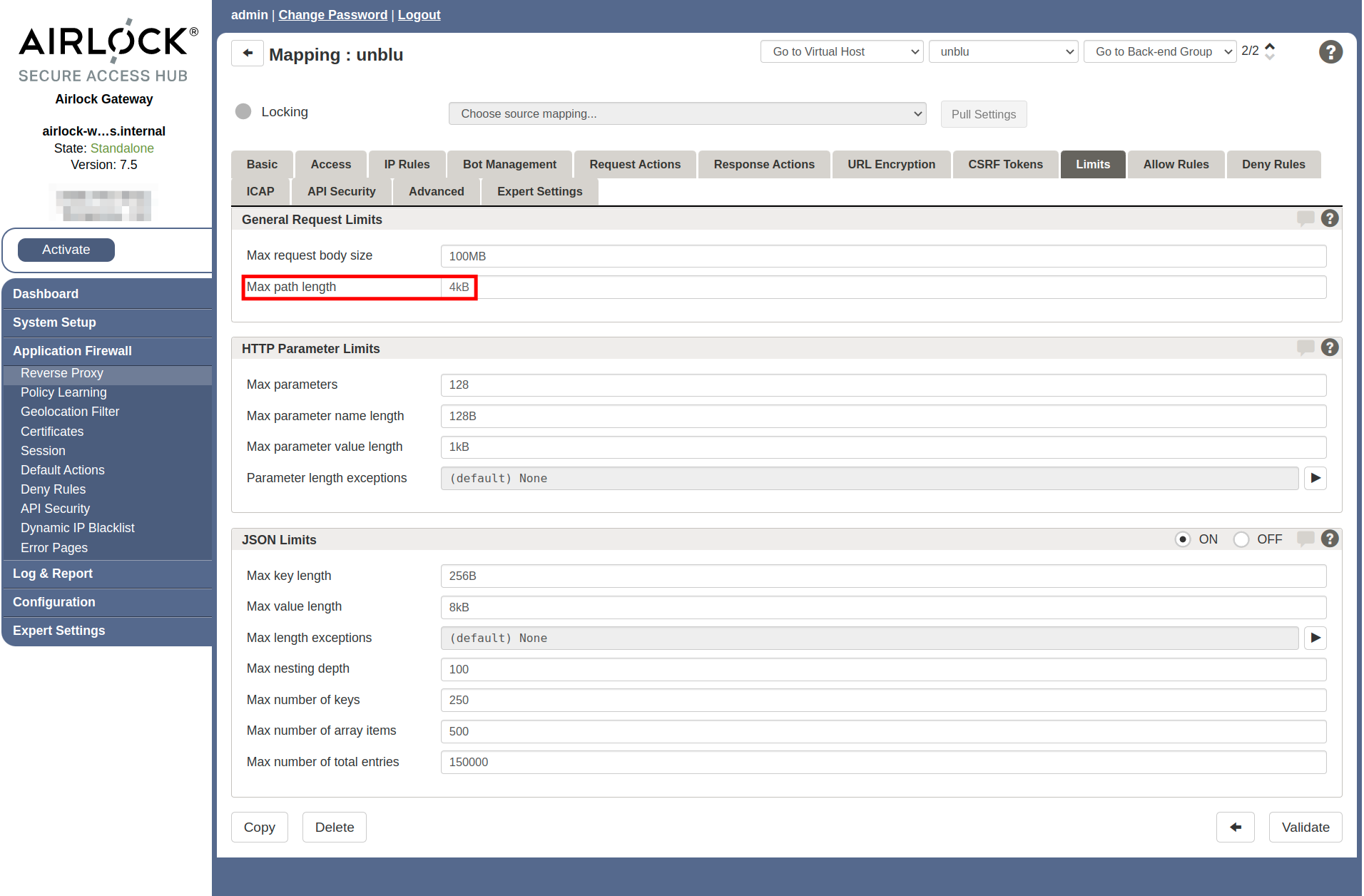
Open the Airlock administration interface and navigate to . Make sure the version of Airlock Gateway you’re using is 5.3 or higher.
Configuring the Airlock Gateway
| Remember to click the Activate button once you’ve finished configuring the Airlock Gateway. |
Configure the Unblu back-end group
-
In the left sidebar of the Airlock administration interface, navigate to .
-
Create the back-end group for the Unblu server if you haven’t already done so.
-
On the Basic tab, fill in the following details:
-
The Name of the group.
-
The appropriate Protocol.
-
The name of your Unblu server’s Back-end host.
-
The Port the Unblu server uses.
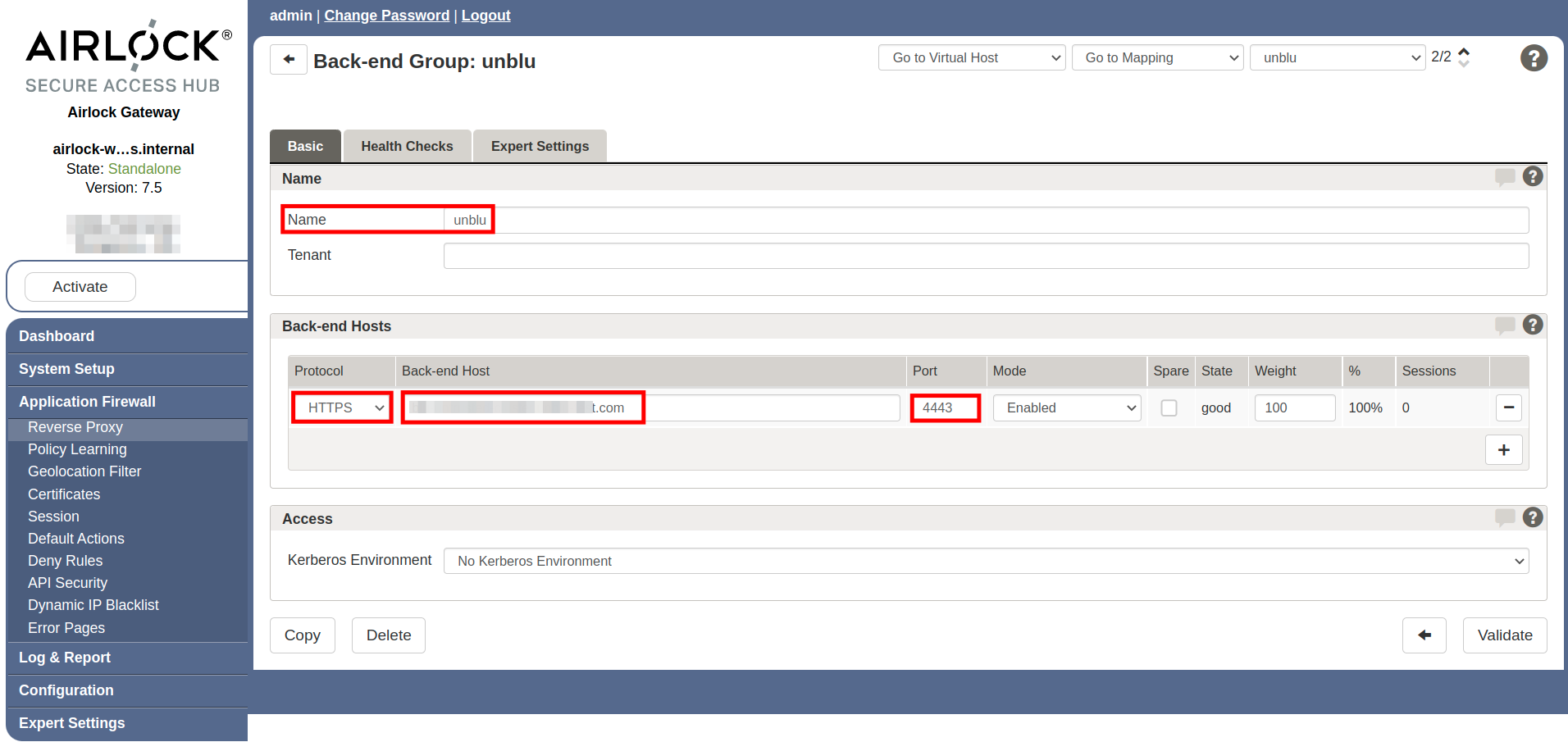 Figure 1. Airlock Unblu back-end group, Basic tab
Figure 1. Airlock Unblu back-end group, Basic tab -
Configure the mapping for the Unblu server
Next, create the mapping for the Unblu server. Start with a new empty mapping. Give it a name that makes it clear which environment and version of Unblu it maps and work through the various tabs as outlined below.
The Basic tab
On the Basic tab, make the following changes:
-
In the Service and Mode section, set the Entry path and the Back-end path to the value of Unblu’s
PUBLICpath prefix as defined in com.unblu.identifier.publicPathPrefix, followed by a trailing slash/. -
In the Application section, set Session handling to Use available session.
-
Set Passthrough cookies to Use regular expression.
-
In the line below the radio button, add the values of the following configuration properties, separated by an OR (
|):-
com.unblu.identifier.singleAccountSessionCookieName or com.unblu.identifier.multiAccountSessionCookieName, depending on whether you have multiple accounts set up on your Unblu server.
With the default values for the configuration properties listed above, the regular expression looks like this:
Listing 1. Regular expression for passthrough cookies with default valuesx-unblu-session | x-unblu-deviceThe default values for the configuration properties above contain variables. In the regular expression, you must replace the variable with its value, like in the example above. -
When you’ve finished, the Basic tab should look like this:

The Request Actions tab
On the Request Actions tab, complete the following steps:
-
Create a custom copy of the (default) Request header whitelist.
-
Adapt the name and add the following headers to the Header Name Pattern:
-
x-unblu-client -
x-unblu-page -
x-unblu-referer -
x-unblu-xui
Separate the header names with an OR (
|). -
-
Make sure you have an action that adds an
X-Forwarded-Protoheader to all requests. The action should look something like this:Request action to add or replace anX-Forwarded-Protoheader to requests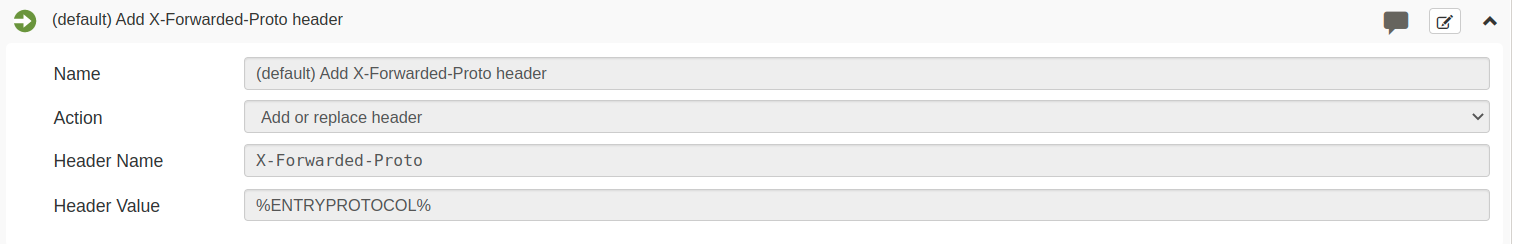
-
Create an action that adds an
X-Forwarded-Hostheader to all requests. The action should look similar to the one that adds anX-Forwarded-Protoheader.
The Response Actions tab
On the Response Actions tab, create a custom copy of the (default) Response header whitelist. Adapt the name and make sure that the Header Name Pattern includes the following headers:
-
Pragma -
Cache-Control -
Expires -
x-unblu-xui -
x-unblu-client -
x-unblu-page -
x-unblu-start-time
Add any missing headers to the pattern with an OR (|).
See also
-
For more information on the Airlock Gateway, refer to the Airlock Secure Access Hub and the hardware requirements.