|
This document describes version 6 of Unblu. If you’re using the latest major version of Unblu, go to the documentation of the latest version. The support period for version 6 ended on 29 August 2023. We no longer provide support or updates for this version. You should upgrade to the latest version of Unblu. |
Hijacking the visitor session
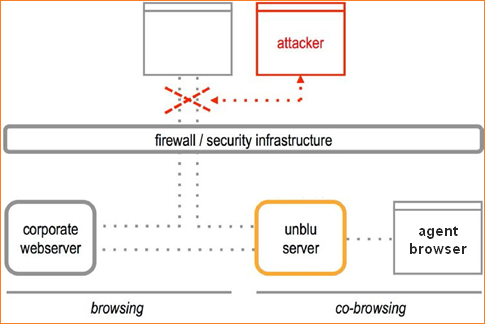
After the visitor logs in, the attacker tries to take over the visitor’s session to perform tasks on the web server, such as executing financial transactions from the visitor’s bank account. There are a number of ways to perform this attack, the most straightforward being to try to guess the session ID. An attacker may also intercept traffic from an unsecured wireless network to try to steal the session ID. Usually, an attacker will not use the session at the same time as the visitor but will wait until after the visitor stops transmitting and before that server closes the session. Alternatively, the attacker could also mount a denial-of-service attack against the visitor’s computer.
How we prevent hijacking of the visitor session
We use your existing network connection for all traffic. Unblu works with all security measures taken to improve connection safety, such as encryption, secure session IDs and secure proxy servers that withhold session data. In addition, we use a few precautions of our own, which help establish a high degree of security even if you do not use secure encryption for your web traffic.
We take the following precautions
-
The collaboration server terminates the co-browsing session if it detects a change in the IP address of the visitor.
-
The collaboration server uses two independent session IDs, one for the session between the server and the visitor, and one for the session between the server and the agent. If an attacker learns one ID, they cannot use it to guess the other.
-
The session ID is independent of the security code the visitor types to connect to the server in the case of a PIN session. If an attacker intercepts the PIN, they cannot use it to guess the session ID.
-
All session IDs are created using the Java Security SecureRandom class, a widely accepted way to create secure session IDs.
-
The client application does not require cookies. This means that you can use a secure proxy server that stores cookies internally and does not give them out to the client.
Can hijacking the visitor session work in the Unblu Financial Cloud?
In the Unblu Financial Cloud, this type of attack is blocked in the same way. However, an on-premises setup allows you to introduce advanced security measures customized to your specific case, which is not possible in the Unblu Financial Cloud.