|
This document describes version 5 of Unblu. If you’re using the latest major version of Unblu, go to the documentation of the latest version. The support period for version 5 ended on 22 November 2021. We no longer provide support or updates for this version. You should upgrade to the latest version of Unblu. |
Eavesdropping on the Visitor Session
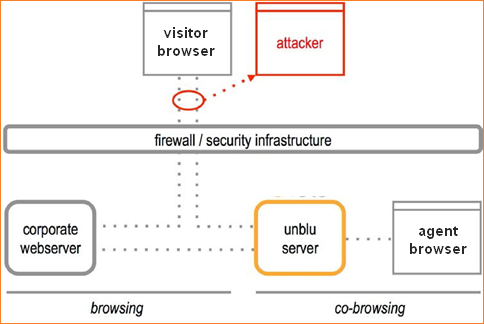
The attacker tries to intercept communication between the visitor and the agent to learn passwords, session information, cookie settings or confidential information between visitor and agent that can be used in a subsequent attack. While an attacker can attempt to eavesdrop on communications at any point, some attack points are more obvious than others, such as when the visitor accesses the company’s web site using an unsecured wireless network.
How we Prevent Eavesdroppers
The collaboration server transmits all data over your secure network connection. It does not make any network connections on its own, and it does not change or restrict the way your secure connection works. In addition, Unblu takes these precautions:
-
We never transmit the content of a password field.
-
We use two independent session IDs, one for the session between the server and the visitor, and one for the session between the server and the agent. If an attacker learns one ID, he or she cannot use it to guess the other.
| The session ID is independent of the PIN the visitor uses to connect to the server. If an attacker intercepts the PIN, he or she cannot use it to guess the session ID. |
-
The client application does not require cookies. This means that you can use a secure proxy server that stores cookies internally and does not hand them out to the client.
-
All session IDs are created using the Java Security SecureRandom class, a widely-accepted way to create secure session IDs.
| If an attacker manages to compromise the safety of the network connection (for example, by hacking the visitor’s computer and logging the keyboard input), using Unblu does not introduce any additional security concerns. We recommend using HTTPS connections for client sessions. Even if you do use unsecured connections, using Unblu does not introduce additional security concerns. |
Can Eavesdropping Succeed in a Cloud Setup?
The collaboration server blocks this type of attack in a cloud setup in the same way as for in an on-premises setup. However, an on-premises setup allows you to introduce an advanced security architecture customized to your specific needs, which is not possible in a cloud setup.