|
This document describes version 5 of Unblu. If you’re using the latest major version of Unblu, go to the documentation of the latest version. The support period for version 5 ended on 22 November 2021. We no longer provide support or updates for this version. You should upgrade to the latest version of Unblu. |
Abusing the Agent Role
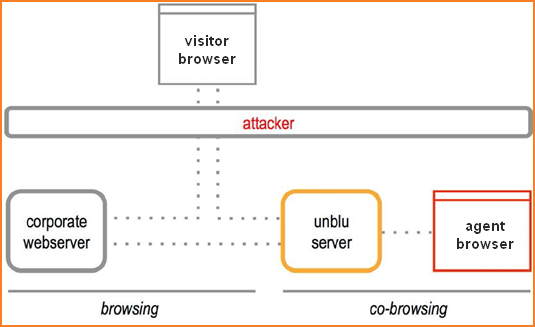
This type of attack assumes that an 'agent' aims to use their position to gain information or money from a visitor. The agent tries to insert information into the visitor’s web content, such as their own account number, or to learn information that they do not otherwise have access to, such as passwords and security questions.
Practically, the agent may ask the visitor to fetch a letter with hopes to execute a financial transaction while the customer is away for a short amount of time.
How we Prevent the Agent Role from Abuse
Unblu has a number of ways to limit the agent’s access to the visitor’s web content:
-
The collaboration server never transmits passwords.
-
Agents cannot modify the content of the visitor’s web page.
-
You can configure the collaboration server to block access to certain data presented through the instrumented web application. For example, the collaboration server may not show the personal settings page of an agent, it may hide account numbers, it may block access to account numbers and payment amounts, and it may prevent agents from executing payments.
| Unblu does not restrict traditional methods of social engineering over the telephone. An agent may still be able to talk a customer into giving away the password or executing specific actions. However, this is possible in all consulting situations, and it is not made easier by using Unblu. |